Check for Spyware using MVT

Why Check for Spyware on Phones?
In today’s digital age, our smartphones hold a wealth of personal information, from photos and messages to banking details and location data. Spyware can compromise this sensitive information, leading to privacy breaches, identity theft, and financial loss. Regularly checking for spyware helps protect your personal data and maintain your device’s security.
Introduction to MVT (Mobile Verification Toolkit)
The Mobile Verification Toolkit (MVT) is an open-source tool designed to help you detect potential spyware on your Android device. Developed by the MVT project, this tool analyzes your device’s logs and backups to identify indicators of compromise. It’s a powerful resource for anyone concerned about their mobile security.
Using WSL on Windows for MVT Installation
While the Mobile Verification Toolkit (MVT) is natively designed for Linux environments, installing it on a Windows machine using Windows Subsystem for Linux (WSL) adds an extra layer of complexity. This approach allows Windows users to leverage the robust capabilities of Linux-based tools without leaving their familiar operating system. By navigating this intricate setup, you can harness the full power of MVT to safeguard your Android device against spyware, all from the comfort of your Windows PC.
Using ADB Over WiFi for MVT
To ensure seamless functionality of the MVT on a Windows machine via WSL, we recommend using ADB over WiFi. This method circumvents the connectivity issues often encountered with WSL. While MVT operates smoothly on native Linux systems, this workaround allows Windows users to achieve similar efficiency.
To get started, download the ADB Shell app from the Google Play Store. This tool will facilitate the necessary communication between your Android device and the MVT, ensuring a robust spyware detection process.
Installation
For detailed instructions on how to install MVT, you can refer to the installation documentation. This guide will walk you through the steps to get MVT up and running on your device.
Install dependencies:
sudo apt install python3 python3-venv python3-pip sqlite3 libusb-1.0-0
python3 -m pip install --user pipx
python3 -m pipx ensurepathInstall MVT:
pipx ensurepath
pipx install mvtEnabling Wireless Debugging for MVT Installation
To facilitate the Mobile Verification Toolkit (MVT) setup, you’ll need to enable wireless debugging on your Android device. This process involves a few straightforward steps:
- Activate Developer Options: First, ensure that Developer Options are enabled on your phone. If not, navigate to your device’s settings, find the ‘About phone’ section, and tap the ‘Build number’ multiple times until Developer Options are activated.
- Enable Wireless Debugging: Within the Developer Options menu, locate and switch on the “Use wireless debugging” feature. This setting allows your device to communicate with your computer over a WiFi network, bypassing the need for a physical USB connection.
- Note the IP Address: Once wireless debugging is enabled, your device will display an IP address. Make a note of this address, as it will be required to establish a connection between your Android device and the MVT tool on your computer.
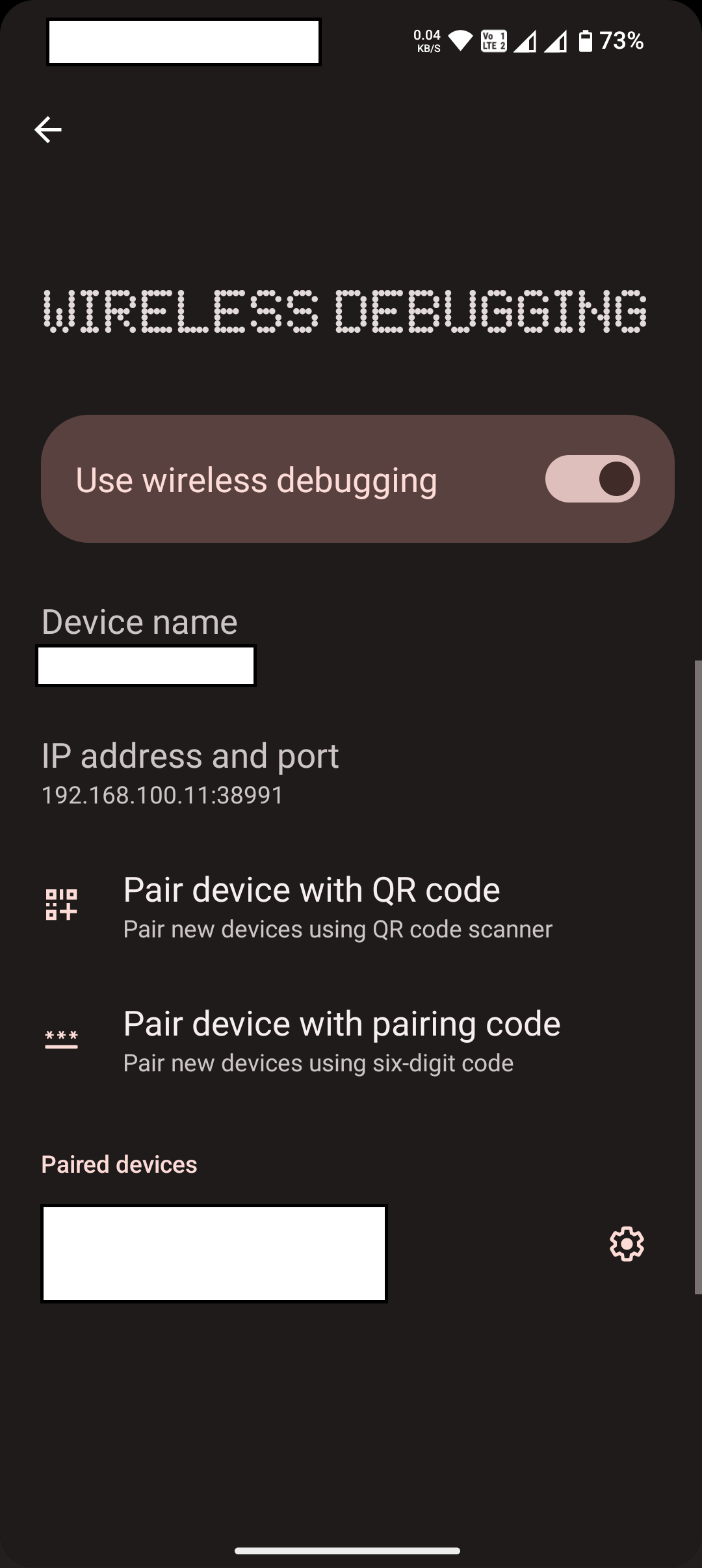
Configuring ADB Shell for Stable Connection
To ensure a stable connection between your Android device and the Mobile Verification Toolkit (MVT), follow these steps:
- Open the ADB Shell App: Launch the ADB Shell app on your Android device.
- Access Local Shell: Navigate to the ‘Local Shell’ option within the app.
- Input Command: Enter the following command to make ADB listen on a fixed port, which helps avoid connection issues and allow debugging:
adb tcpip 5555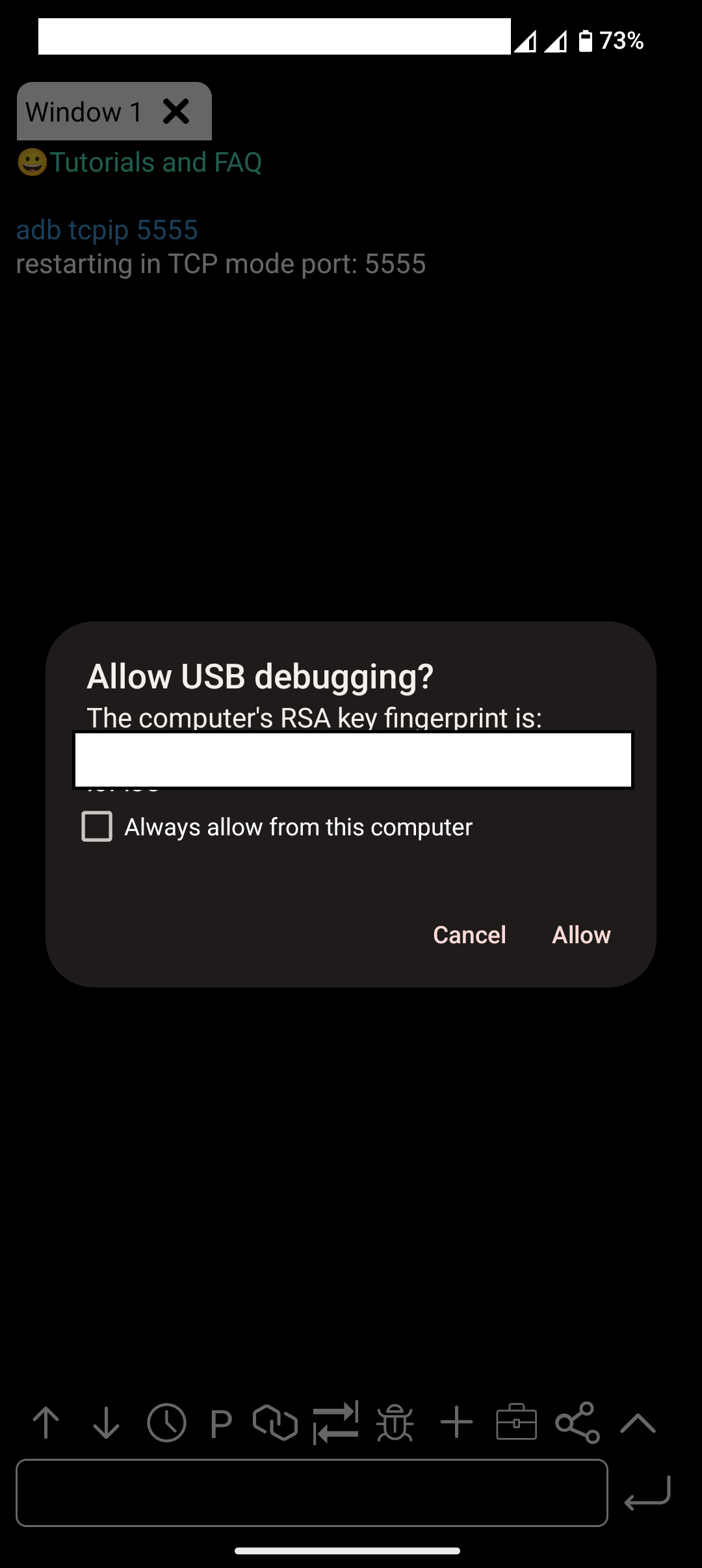
Running MVT for Spyware Analysis
With your Android device connected via ADB over WiFi, you’re ready to run the Mobile Verification Toolkit (MVT) to analyze your device for potential spyware. Follow these steps:
First you should download the Structured Threat Information Expression (STIX) files to identify potential traces of compromise.:
mvt-android download-iocsOpen your terminal and input the following command:
mvt-android check-adb --serial 192.168.100.11:5555 --output /path/tofileAfter a few minutes you see that backup is requested both in the shell and on your mobile phone
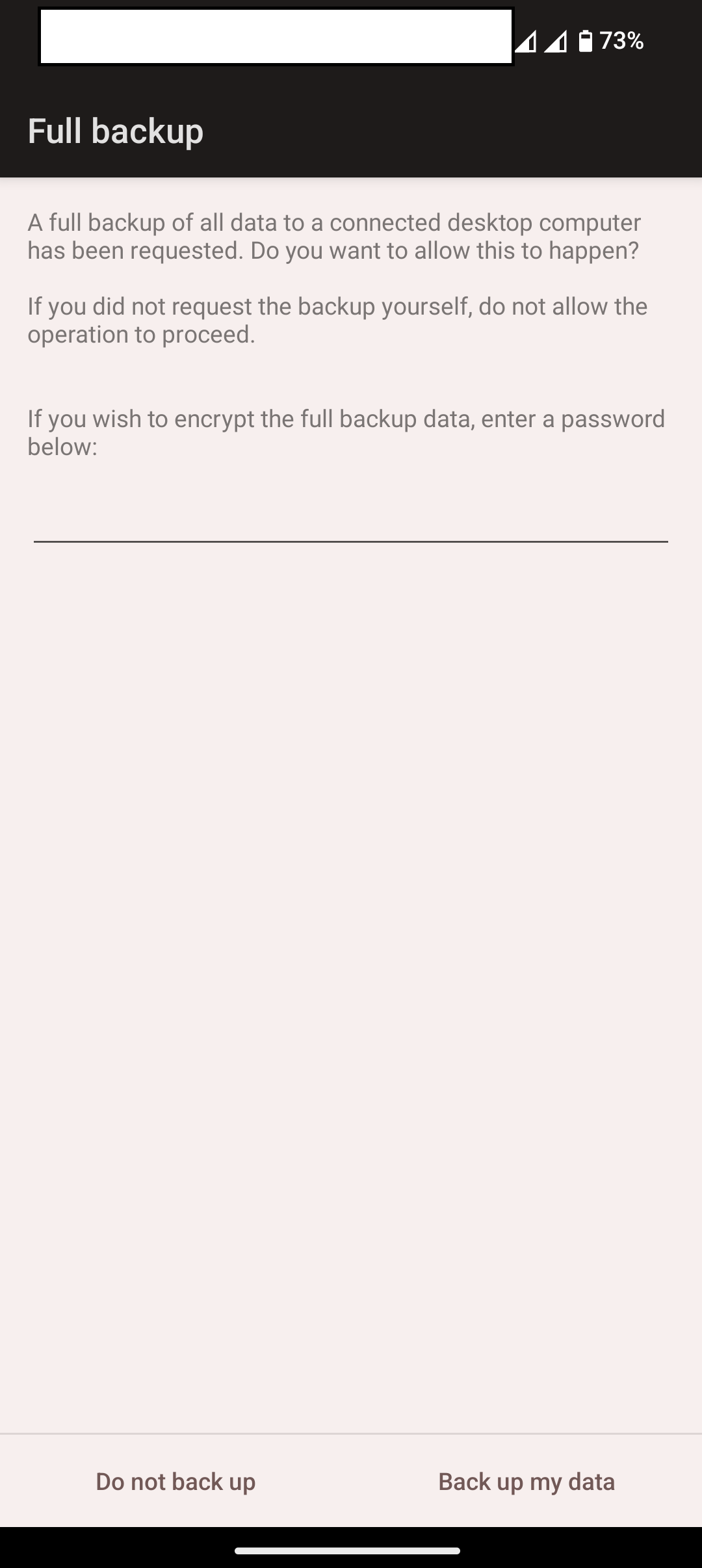
You can either set a password or not, it will not affect the analysis.
Wait for it to complete.
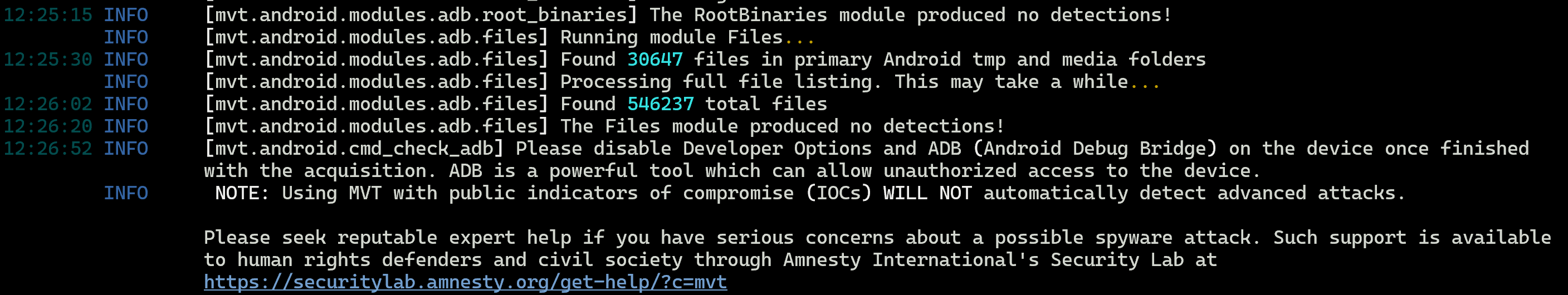
You will see it has retrieved your messages, applications installed, what applications has potentially dangerous permissions, if nothing detected it will have message "produced no detections", etc...
NOTE: Please seek reputable expert help if you have serious concerns about a possible spyware attack. Such support is available to human rights defenders and civil society through Amnesty International's Security Lab at
https://securitylab.amnesty.org/get-help/?c=mvt